mirror of
https://github.com/openfaas/faasd.git
synced 2025-06-21 08:16:34 +00:00
Compare commits
15 Commits
0.14.2
...
0.15.0-rc1
| Author | SHA1 | Date | |
|---|---|---|---|
| 77867f17e3 | |||
| 5aed707354 | |||
| 8fbdd1a461 | |||
| 8dd48b8957 | |||
| 6763ed6d66 | |||
| acb5d0bd1c | |||
| 2c9eb3904e | |||
| b42066d1a1 | |||
| 17188b8de9 | |||
| 0c0088e8b0 | |||
| c5f167df21 | |||
| d5fcc7b2ab | |||
| cbfefb6fa5 | |||
| ea62c1b12d | |||
| 8f40618a5c |
2
.github/workflows/build.yaml
vendored
2
.github/workflows/build.yaml
vendored
@ -12,7 +12,7 @@ jobs:
|
|||||||
GO111MODULE: off
|
GO111MODULE: off
|
||||||
strategy:
|
strategy:
|
||||||
matrix:
|
matrix:
|
||||||
go-version: [1.16.x]
|
go-version: [1.17.x]
|
||||||
os: [ubuntu-latest]
|
os: [ubuntu-latest]
|
||||||
runs-on: ${{ matrix.os }}
|
runs-on: ${{ matrix.os }}
|
||||||
steps:
|
steps:
|
||||||
|
|||||||
2
.github/workflows/publish.yaml
vendored
2
.github/workflows/publish.yaml
vendored
@ -9,7 +9,7 @@ jobs:
|
|||||||
publish:
|
publish:
|
||||||
strategy:
|
strategy:
|
||||||
matrix:
|
matrix:
|
||||||
go-version: [ 1.16.x ]
|
go-version: [ 1.17.x ]
|
||||||
os: [ ubuntu-latest ]
|
os: [ ubuntu-latest ]
|
||||||
runs-on: ${{ matrix.os }}
|
runs-on: ${{ matrix.os }}
|
||||||
steps:
|
steps:
|
||||||
|
|||||||
@ -1,5 +1,6 @@
|
|||||||
# faasd - a lightweight & portable faas engine
|
# faasd - a lightweight & portable faas engine
|
||||||
|
|
||||||
|
[](https://github.com/sponsors/openfaas)
|
||||||
[](https://github.com/openfaas/faasd/actions)
|
[](https://github.com/openfaas/faasd/actions)
|
||||||
[](https://opensource.org/licenses/MIT)
|
[](https://opensource.org/licenses/MIT)
|
||||||
[](https://www.openfaas.com)
|
[](https://www.openfaas.com)
|
||||||
@ -44,7 +45,7 @@ Additional resources:
|
|||||||
|
|
||||||
Most importantly, it's easy to manage so you can set it up and leave it alone to run your functions.
|
Most importantly, it's easy to manage so you can set it up and leave it alone to run your functions.
|
||||||
|
|
||||||
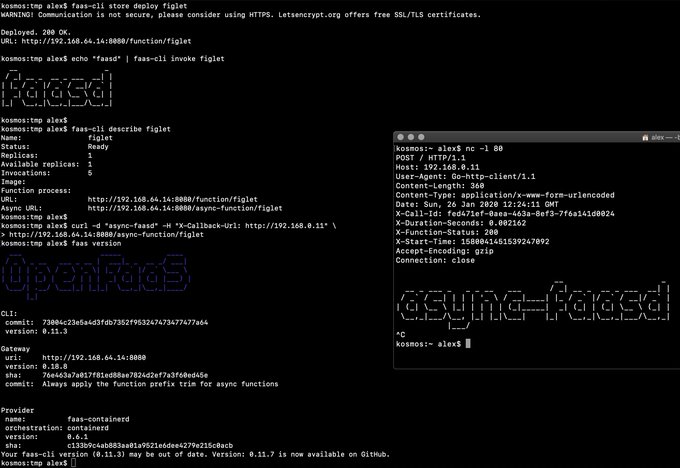
|
[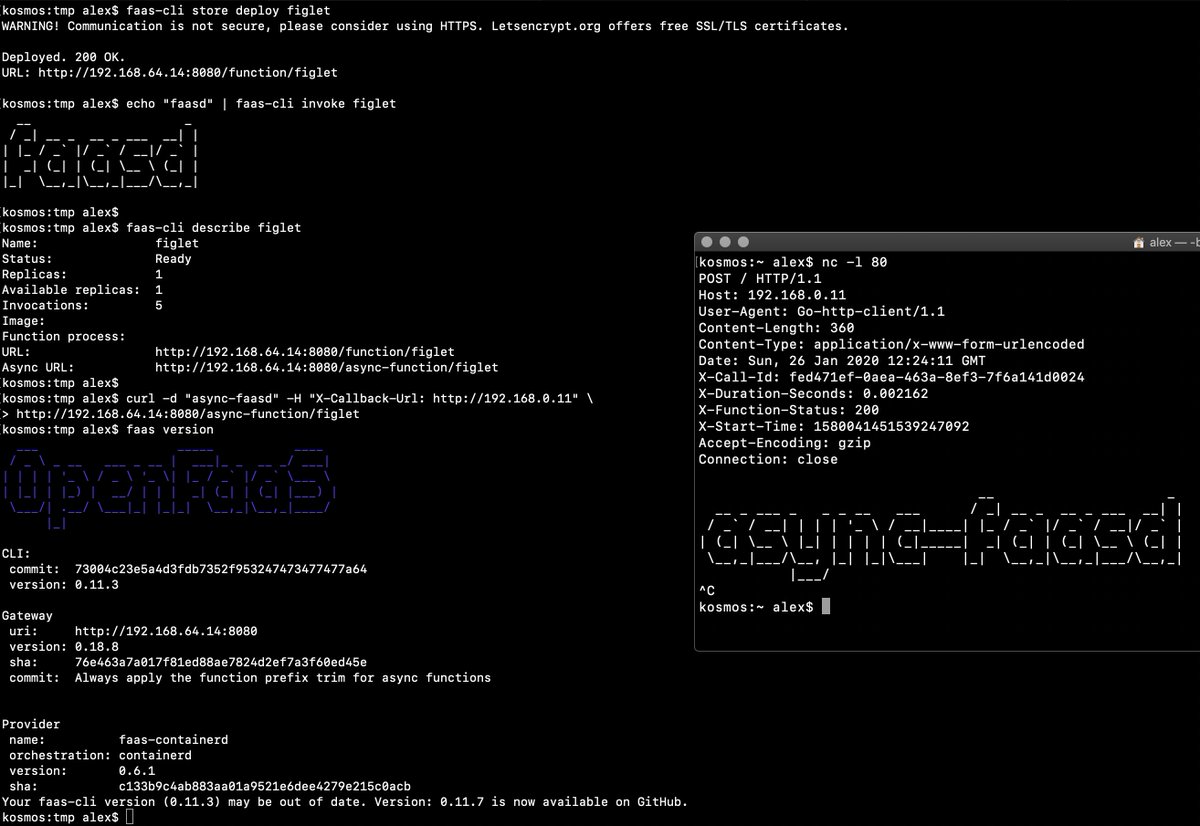](https://www.youtube.com/watch?v=WX1tZoSXy8E)
|
||||||
|
|
||||||
> Demo of faasd running asynchronous functions
|
> Demo of faasd running asynchronous functions
|
||||||
|
|
||||||
@ -166,4 +167,6 @@ For completed features, WIP and upcoming roadmap see:
|
|||||||
|
|
||||||
See [ROADMAP.md](docs/ROADMAP.md)
|
See [ROADMAP.md](docs/ROADMAP.md)
|
||||||
|
|
||||||
|
Want to build a patch without setting up a complete development environment? See [docs/PATCHES.md](docs/PATCHES.md)
|
||||||
|
|
||||||
Are you looking to hack on faasd? Follow the [developer instructions](docs/DEV.md) for a manual installation, or use the `hack/install.sh` script and pick up from there.
|
Are you looking to hack on faasd? Follow the [developer instructions](docs/DEV.md) for a manual installation, or use the `hack/install.sh` script and pick up from there.
|
||||||
|
|||||||
@ -20,21 +20,36 @@ services:
|
|||||||
|
|
||||||
nats:
|
nats:
|
||||||
image: docker.io/library/nats-streaming:0.22.0
|
image: docker.io/library/nats-streaming:0.22.0
|
||||||
|
# nobody
|
||||||
|
user: "65534"
|
||||||
command:
|
command:
|
||||||
- "/nats-streaming-server"
|
- "/nats-streaming-server"
|
||||||
- "-m"
|
- "-m"
|
||||||
- "8222"
|
- "8222"
|
||||||
- "--store=memory"
|
- "--store=file"
|
||||||
|
- "--dir=/nats"
|
||||||
- "--cluster_id=faas-cluster"
|
- "--cluster_id=faas-cluster"
|
||||||
|
volumes:
|
||||||
|
# Data directory
|
||||||
|
- type: bind
|
||||||
|
source: ./nats
|
||||||
|
target: /nats
|
||||||
# ports:
|
# ports:
|
||||||
# - "127.0.0.1:8222:8222"
|
# - "127.0.0.1:8222:8222"
|
||||||
|
|
||||||
prometheus:
|
prometheus:
|
||||||
image: docker.io/prom/prometheus:v2.14.0
|
image: docker.io/prom/prometheus:v2.14.0
|
||||||
|
# nobody
|
||||||
|
user: "65534"
|
||||||
volumes:
|
volumes:
|
||||||
|
# Config directory
|
||||||
- type: bind
|
- type: bind
|
||||||
source: ./prometheus.yml
|
source: ./prometheus.yml
|
||||||
target: /etc/prometheus/prometheus.yml
|
target: /etc/prometheus/prometheus.yml
|
||||||
|
# Data directory
|
||||||
|
- type: bind
|
||||||
|
source: ./prometheus
|
||||||
|
target: /prometheus
|
||||||
cap_add:
|
cap_add:
|
||||||
- CAP_NET_RAW
|
- CAP_NET_RAW
|
||||||
ports:
|
ports:
|
||||||
|
|||||||
@ -1,7 +1,11 @@
|
|||||||
## Instructions for hacking on faasd itself
|
## Instructions for building and testing faasd locally
|
||||||
|
|
||||||
> Note: if you're just wanting to try out faasd, then it's likely that you're on the wrong page. This is a detailed set of instructions for those wanting to contribute or customise faasd. Feel free to go back to the homepage and pick a tutorial instead.
|
> Note: if you're just wanting to try out faasd, then it's likely that you're on the wrong page. This is a detailed set of instructions for those wanting to contribute or customise faasd. Feel free to go back to the homepage and pick a tutorial instead.
|
||||||
|
|
||||||
|
Do you want to help the community test a pull request?
|
||||||
|
|
||||||
|
See these instructions instead: [Testing patches](/docs/PATCHES.md)
|
||||||
|
|
||||||
### Pre-reqs
|
### Pre-reqs
|
||||||
|
|
||||||
> It's recommended that you do not install Docker on the same host as faasd, since 1) they may both use different versions of containerd and 2) docker's networking rules can disrupt faasd's networking. When using faasd - make your faasd server a faasd server, and build container image on your laptop or in a CI pipeline.
|
> It's recommended that you do not install Docker on the same host as faasd, since 1) they may both use different versions of containerd and 2) docker's networking rules can disrupt faasd's networking. When using faasd - make your faasd server a faasd server, and build container image on your laptop or in a CI pipeline.
|
||||||
|
|||||||
88
docs/PATCHES.md
Normal file
88
docs/PATCHES.md
Normal file
@ -0,0 +1,88 @@
|
|||||||
|
## Instructions for testing a patch for faasd
|
||||||
|
|
||||||
|
### Launch a virtual machine
|
||||||
|
|
||||||
|
You can use any kind of Linux virtual machine, Ubuntu 20.04 is recommended.
|
||||||
|
|
||||||
|
Launch a cloud VM or use [Multipass](https://multipass.run), which is free to use an can be run locally. A Raspberry Pi 3 or 4 could also be used, but will need you to run `make dist` to cross compile a valid binary.
|
||||||
|
|
||||||
|
### Copy over your SSH key
|
||||||
|
|
||||||
|
Your SSH key will be used, so that you can copy a new faasd binary over to the host.
|
||||||
|
|
||||||
|
```bash
|
||||||
|
multipass launch \
|
||||||
|
--mem 4G \
|
||||||
|
-c 2 \
|
||||||
|
-n faasd
|
||||||
|
|
||||||
|
# Then access its shell
|
||||||
|
multipass shell faasd
|
||||||
|
|
||||||
|
# Edit .ssh/authorized_keys
|
||||||
|
|
||||||
|
# Add .ssh/id_rsa.pub from your host and save the file
|
||||||
|
```
|
||||||
|
|
||||||
|
### Install faasd on the VM
|
||||||
|
|
||||||
|
You start off with the upstream version of faasd on the host, then add the new version over the top later on.
|
||||||
|
|
||||||
|
```bash
|
||||||
|
cd /tmp/
|
||||||
|
git clone https://github.com/openfaas/faasd --depth=1
|
||||||
|
cd faasd/hack
|
||||||
|
./install.sh
|
||||||
|
|
||||||
|
# Run the login command given to you at the end of the script
|
||||||
|
```
|
||||||
|
|
||||||
|
Get the multipass IP address:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
export IP=$(multipass info faasd --format json| jq -r '.info.faasd.ipv4[0]')
|
||||||
|
```
|
||||||
|
|
||||||
|
### Build a new faasd binary with the patch
|
||||||
|
|
||||||
|
Check out faasd on your local computer
|
||||||
|
|
||||||
|
```bash
|
||||||
|
git clone https://github.com/openfaas/faasd
|
||||||
|
cd faasd
|
||||||
|
|
||||||
|
gh pr checkout #PR_NUMBER_HERE
|
||||||
|
|
||||||
|
GOOS=linux go build
|
||||||
|
|
||||||
|
# You can also run "make dist" which is slower, but includes
|
||||||
|
# a version and binaries for other platforms such as the Raspberry Pi
|
||||||
|
```
|
||||||
|
|
||||||
|
### Copy it over to the VM
|
||||||
|
|
||||||
|
Now build a new faasd binary and copy it to the VM:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
scp faasd ubuntu@$IP:~/
|
||||||
|
```
|
||||||
|
|
||||||
|
Now deploy the new version on the VM:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
killall -9 faasd-linux; killall -9 faasd-linux ; mv ./faasd-linux /usr/local/bin/faasd
|
||||||
|
```
|
||||||
|
|
||||||
|
### Check it worked and test that patch
|
||||||
|
|
||||||
|
Now run a command with `faas-cli` such as:
|
||||||
|
|
||||||
|
* `faas-cli list`
|
||||||
|
* `faas-cli version`
|
||||||
|
|
||||||
|
See the testing instructions on the PR and run through those steps.
|
||||||
|
|
||||||
|
Post your results on GitHub to assist the creator of the pull request.
|
||||||
|
|
||||||
|
You can see how to get the logs for various components using the [eBook Serverless For Everyone Else](https://gumroad.com/l/serverless-for-everyone-else), or by consulting the [DEV.md](/docs/DEV.md) guide.
|
||||||
|
|
||||||
@ -75,10 +75,10 @@ sudo systemctl restart faasd
|
|||||||
|
|
||||||
Should have:
|
Should have:
|
||||||
|
|
||||||
* [ ] Resolve core services from functions by populating/sharing `/etc/hosts` between `faasd` and `faasd-provider`
|
* [ ] Offer a recommendation or implement a strategy for faasd replication/HA
|
||||||
* [ ] Docs or examples on how to use the various connectors and connector-sdk
|
|
||||||
* [ ] Monitor and restart any of the core components at runtime if the container stops
|
* [ ] Monitor and restart any of the core components at runtime if the container stops
|
||||||
* [ ] Asynchronous deletion instead of synchronous
|
* [ ] Asynchronous function deletion instead of synchronous
|
||||||
|
* [ ] Asynchronous function start-up instead of synchronous
|
||||||
|
|
||||||
Nice to Have:
|
Nice to Have:
|
||||||
|
|
||||||
@ -89,6 +89,8 @@ Nice to Have:
|
|||||||
|
|
||||||
### Completed
|
### Completed
|
||||||
|
|
||||||
|
* [x] Docs or examples on how to use the various event connectors (Yes in the eBook)
|
||||||
|
* [x] Resolve core services from functions by populating/sharing `/etc/hosts` between `faasd` and `faasd-provider`
|
||||||
* [x] Provide a cloud-init configuration for faasd bootstrap
|
* [x] Provide a cloud-init configuration for faasd bootstrap
|
||||||
* [x] Configure core services from a docker-compose.yaml file
|
* [x] Configure core services from a docker-compose.yaml file
|
||||||
* [x] Store and fetch logs from the journal
|
* [x] Store and fetch logs from the journal
|
||||||
|
|||||||
@ -29,6 +29,7 @@ type Function struct {
|
|||||||
secrets []string
|
secrets []string
|
||||||
envVars map[string]string
|
envVars map[string]string
|
||||||
envProcess string
|
envProcess string
|
||||||
|
memoryLimit int64
|
||||||
createdAt time.Time
|
createdAt time.Time
|
||||||
}
|
}
|
||||||
|
|
||||||
@ -92,7 +93,7 @@ func GetFunction(client *containerd.Client, name string, namespace string) (Func
|
|||||||
|
|
||||||
spec, err := c.Spec(ctx)
|
spec, err := c.Spec(ctx)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return Function{}, fmt.Errorf("unable to load function spec for reading secrets: %s, error %w", name, err)
|
return Function{}, fmt.Errorf("unable to load function %s error: %w", name, err)
|
||||||
}
|
}
|
||||||
|
|
||||||
info, err := c.Info(ctx)
|
info, err := c.Info(ctx)
|
||||||
@ -112,6 +113,7 @@ func GetFunction(client *containerd.Client, name string, namespace string) (Func
|
|||||||
fn.envVars = envVars
|
fn.envVars = envVars
|
||||||
fn.envProcess = envProcess
|
fn.envProcess = envProcess
|
||||||
fn.createdAt = info.CreatedAt
|
fn.createdAt = info.CreatedAt
|
||||||
|
fn.memoryLimit = readMemoryLimitFromSpec(spec)
|
||||||
|
|
||||||
replicas := 0
|
replicas := 0
|
||||||
task, err := c.Task(ctx, nil)
|
task, err := c.Task(ctx, nil)
|
||||||
@ -231,3 +233,10 @@ func findNamespace(target string, items []string) bool {
|
|||||||
}
|
}
|
||||||
return false
|
return false
|
||||||
}
|
}
|
||||||
|
|
||||||
|
func readMemoryLimitFromSpec(spec *specs.Spec) int64 {
|
||||||
|
if spec.Linux == nil || spec.Linux.Resources == nil || spec.Linux.Resources.Memory == nil || spec.Linux.Resources.Memory.Limit == nil {
|
||||||
|
return 0
|
||||||
|
}
|
||||||
|
return *spec.Linux.Resources.Memory.Limit
|
||||||
|
}
|
||||||
|
|||||||
@ -32,54 +32,54 @@ func Test_BuildLabelsAndAnnotationsFromServiceSpec_Annotations(t *testing.T) {
|
|||||||
}
|
}
|
||||||
|
|
||||||
func Test_SplitMountToSecrets(t *testing.T) {
|
func Test_SplitMountToSecrets(t *testing.T) {
|
||||||
type test struct {
|
type testCase struct {
|
||||||
Name string
|
Name string
|
||||||
Input []specs.Mount
|
Input []specs.Mount
|
||||||
Expected []string
|
Want []string
|
||||||
}
|
}
|
||||||
tests := []test{
|
tests := []testCase{
|
||||||
{Name: "No matching openfaas secrets", Input: []specs.Mount{{Destination: "/foo/"}}, Expected: []string{}},
|
{Name: "No matching openfaas secrets", Input: []specs.Mount{{Destination: "/foo/"}}, Want: []string{}},
|
||||||
{Name: "Nil mounts", Input: nil, Expected: []string{}},
|
{Name: "Nil mounts", Input: nil, Want: []string{}},
|
||||||
{Name: "No Mounts", Input: []specs.Mount{{Destination: "/foo/"}}, Expected: []string{}},
|
{Name: "No Mounts", Input: []specs.Mount{{Destination: "/foo/"}}, Want: []string{}},
|
||||||
{Name: "One Mounts IS secret", Input: []specs.Mount{{Destination: "/var/openfaas/secrets/secret1"}}, Expected: []string{"secret1"}},
|
{Name: "One Mounts IS secret", Input: []specs.Mount{{Destination: "/var/openfaas/secrets/secret1"}}, Want: []string{"secret1"}},
|
||||||
{Name: "Multiple Mounts 1 secret", Input: []specs.Mount{{Destination: "/var/openfaas/secrets/secret1"}, {Destination: "/some/other/path"}}, Expected: []string{"secret1"}},
|
{Name: "Multiple Mounts 1 secret", Input: []specs.Mount{{Destination: "/var/openfaas/secrets/secret1"}, {Destination: "/some/other/path"}}, Want: []string{"secret1"}},
|
||||||
{Name: "Multiple Mounts all secrets", Input: []specs.Mount{{Destination: "/var/openfaas/secrets/secret1"}, {Destination: "/var/openfaas/secrets/secret2"}}, Expected: []string{"secret1", "secret2"}},
|
{Name: "Multiple Mounts all secrets", Input: []specs.Mount{{Destination: "/var/openfaas/secrets/secret1"}, {Destination: "/var/openfaas/secrets/secret2"}}, Want: []string{"secret1", "secret2"}},
|
||||||
}
|
}
|
||||||
|
|
||||||
for _, tc := range tests {
|
for _, tc := range tests {
|
||||||
t.Run(tc.Name, func(t *testing.T) {
|
t.Run(tc.Name, func(t *testing.T) {
|
||||||
got := readSecretsFromMounts(tc.Input)
|
got := readSecretsFromMounts(tc.Input)
|
||||||
if !reflect.DeepEqual(got, tc.Expected) {
|
if !reflect.DeepEqual(got, tc.Want) {
|
||||||
t.Fatalf("expected %s, got %s", tc.Expected, got)
|
t.Fatalf("Want %s, got %s", tc.Want, got)
|
||||||
}
|
}
|
||||||
})
|
})
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
func Test_ProcessEnvToEnvVars(t *testing.T) {
|
func Test_ProcessEnvToEnvVars(t *testing.T) {
|
||||||
type test struct {
|
type testCase struct {
|
||||||
Name string
|
Name string
|
||||||
Input []string
|
Input []string
|
||||||
Expected map[string]string
|
Want map[string]string
|
||||||
fprocess string
|
fprocess string
|
||||||
}
|
}
|
||||||
tests := []test{
|
tests := []testCase{
|
||||||
{Name: "No matching EnvVars", Input: []string{"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "fprocess=python index.py"}, Expected: make(map[string]string), fprocess: "python index.py"},
|
{Name: "No matching EnvVars", Input: []string{"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "fprocess=python index.py"}, Want: make(map[string]string), fprocess: "python index.py"},
|
||||||
{Name: "No EnvVars", Input: []string{}, Expected: make(map[string]string), fprocess: ""},
|
{Name: "No EnvVars", Input: []string{}, Want: make(map[string]string), fprocess: ""},
|
||||||
{Name: "One EnvVar", Input: []string{"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "fprocess=python index.py", "env=this"}, Expected: map[string]string{"env": "this"}, fprocess: "python index.py"},
|
{Name: "One EnvVar", Input: []string{"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "fprocess=python index.py", "env=this"}, Want: map[string]string{"env": "this"}, fprocess: "python index.py"},
|
||||||
{Name: "Multiple EnvVars", Input: []string{"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "this=that", "env=var", "fprocess=python index.py"}, Expected: map[string]string{"this": "that", "env": "var"}, fprocess: "python index.py"},
|
{Name: "Multiple EnvVars", Input: []string{"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "this=that", "env=var", "fprocess=python index.py"}, Want: map[string]string{"this": "that", "env": "var"}, fprocess: "python index.py"},
|
||||||
{Name: "Nil EnvVars", Input: nil, Expected: make(map[string]string)},
|
{Name: "Nil EnvVars", Input: nil, Want: make(map[string]string)},
|
||||||
}
|
}
|
||||||
|
|
||||||
for _, tc := range tests {
|
for _, tc := range tests {
|
||||||
t.Run(tc.Name, func(t *testing.T) {
|
t.Run(tc.Name, func(t *testing.T) {
|
||||||
got, fprocess := readEnvFromProcessEnv(tc.Input)
|
got, fprocess := readEnvFromProcessEnv(tc.Input)
|
||||||
if !reflect.DeepEqual(got, tc.Expected) {
|
if !reflect.DeepEqual(got, tc.Want) {
|
||||||
t.Fatalf("expected: %s, got: %s", tc.Expected, got)
|
t.Fatalf("Want: %s, got: %s", tc.Want, got)
|
||||||
}
|
}
|
||||||
|
|
||||||
if fprocess != tc.fprocess {
|
if fprocess != tc.fprocess {
|
||||||
t.Fatalf("expected fprocess: %s, got: %s", tc.fprocess, got)
|
t.Fatalf("Want fprocess: %s, got: %s", tc.fprocess, got)
|
||||||
|
|
||||||
}
|
}
|
||||||
})
|
})
|
||||||
@ -87,22 +87,46 @@ func Test_ProcessEnvToEnvVars(t *testing.T) {
|
|||||||
}
|
}
|
||||||
|
|
||||||
func Test_findNamespace(t *testing.T) {
|
func Test_findNamespace(t *testing.T) {
|
||||||
type test struct {
|
type testCase struct {
|
||||||
Name string
|
Name string
|
||||||
foundNamespaces []string
|
foundNamespaces []string
|
||||||
namespace string
|
namespace string
|
||||||
Expected bool
|
Want bool
|
||||||
}
|
}
|
||||||
tests := []test{
|
tests := []testCase{
|
||||||
{Name: "Namespace Found", namespace: "fn", foundNamespaces: []string{"fn", "openfaas-fn"}, Expected: true},
|
{Name: "Namespace Found", namespace: "fn", foundNamespaces: []string{"fn", "openfaas-fn"}, Want: true},
|
||||||
{Name: "namespace Not Found", namespace: "fn", foundNamespaces: []string{"openfaas-fn"}, Expected: false},
|
{Name: "namespace Not Found", namespace: "fn", foundNamespaces: []string{"openfaas-fn"}, Want: false},
|
||||||
}
|
}
|
||||||
|
|
||||||
for _, tc := range tests {
|
for _, tc := range tests {
|
||||||
t.Run(tc.Name, func(t *testing.T) {
|
t.Run(tc.Name, func(t *testing.T) {
|
||||||
got := findNamespace(tc.namespace, tc.foundNamespaces)
|
got := findNamespace(tc.namespace, tc.foundNamespaces)
|
||||||
if got != tc.Expected {
|
if got != tc.Want {
|
||||||
t.Fatalf("expected %t, got %t", tc.Expected, got)
|
t.Fatalf("Want %t, got %t", tc.Want, got)
|
||||||
|
}
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
func Test_readMemoryLimitFromSpec(t *testing.T) {
|
||||||
|
type testCase struct {
|
||||||
|
Name string
|
||||||
|
Spec *specs.Spec
|
||||||
|
Want int64
|
||||||
|
}
|
||||||
|
testLimit := int64(64)
|
||||||
|
tests := []testCase{
|
||||||
|
{Name: "specs.Linux not found", Spec: &specs.Spec{Linux: nil}, Want: int64(0)},
|
||||||
|
{Name: "specs.LinuxResource not found", Spec: &specs.Spec{Linux: &specs.Linux{Resources: nil}}, Want: int64(0)},
|
||||||
|
{Name: "specs.LinuxMemory not found", Spec: &specs.Spec{Linux: &specs.Linux{Resources: &specs.LinuxResources{Memory: nil}}}, Want: int64(0)},
|
||||||
|
{Name: "specs.LinuxMemory.Limit not found", Spec: &specs.Spec{Linux: &specs.Linux{Resources: &specs.LinuxResources{Memory: &specs.LinuxMemory{Limit: nil}}}}, Want: int64(0)},
|
||||||
|
{Name: "Memory limit set as Want", Spec: &specs.Spec{Linux: &specs.Linux{Resources: &specs.LinuxResources{Memory: &specs.LinuxMemory{Limit: &testLimit}}}}, Want: int64(64)},
|
||||||
|
}
|
||||||
|
for _, tc := range tests {
|
||||||
|
t.Run(tc.Name, func(t *testing.T) {
|
||||||
|
got := readMemoryLimitFromSpec(tc.Spec)
|
||||||
|
if got != tc.Want {
|
||||||
|
t.Fatalf("Want %d, got %d", tc.Want, got)
|
||||||
}
|
}
|
||||||
})
|
})
|
||||||
}
|
}
|
||||||
|
|||||||
@ -2,6 +2,7 @@ package handlers
|
|||||||
|
|
||||||
import (
|
import (
|
||||||
"encoding/json"
|
"encoding/json"
|
||||||
|
"k8s.io/apimachinery/pkg/api/resource"
|
||||||
"log"
|
"log"
|
||||||
"net/http"
|
"net/http"
|
||||||
|
|
||||||
@ -37,6 +38,7 @@ func MakeReadHandler(client *containerd.Client) func(w http.ResponseWriter, r *h
|
|||||||
for _, fn := range fns {
|
for _, fn := range fns {
|
||||||
annotations := &fn.annotations
|
annotations := &fn.annotations
|
||||||
labels := &fn.labels
|
labels := &fn.labels
|
||||||
|
memory := resource.NewQuantity(fn.memoryLimit, resource.BinarySI)
|
||||||
res = append(res, types.FunctionStatus{
|
res = append(res, types.FunctionStatus{
|
||||||
Name: fn.name,
|
Name: fn.name,
|
||||||
Image: fn.image,
|
Image: fn.image,
|
||||||
@ -47,6 +49,7 @@ func MakeReadHandler(client *containerd.Client) func(w http.ResponseWriter, r *h
|
|||||||
Secrets: fn.secrets,
|
Secrets: fn.secrets,
|
||||||
EnvVars: fn.envVars,
|
EnvVars: fn.envVars,
|
||||||
EnvProcess: fn.envProcess,
|
EnvProcess: fn.envProcess,
|
||||||
|
Limits: &types.FunctionResources{Memory: memory.String()},
|
||||||
CreatedAt: fn.createdAt,
|
CreatedAt: fn.createdAt,
|
||||||
})
|
})
|
||||||
}
|
}
|
||||||
|
|||||||
@ -86,6 +86,14 @@ func createSecret(c *containerd.Client, w http.ResponseWriter, r *http.Request,
|
|||||||
return
|
return
|
||||||
}
|
}
|
||||||
|
|
||||||
|
err = validateSecret(secret)
|
||||||
|
if err != nil {
|
||||||
|
log.Printf("[secret] error %s", err.Error())
|
||||||
|
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||||
|
return
|
||||||
|
}
|
||||||
|
|
||||||
|
log.Printf("[secret] is valid: %q", secret.Name)
|
||||||
namespace := getRequestNamespace(secret.Namespace)
|
namespace := getRequestNamespace(secret.Namespace)
|
||||||
mountPath = getNamespaceSecretMountPath(mountPath, namespace)
|
mountPath = getNamespaceSecretMountPath(mountPath, namespace)
|
||||||
|
|
||||||
@ -96,7 +104,12 @@ func createSecret(c *containerd.Client, w http.ResponseWriter, r *http.Request,
|
|||||||
return
|
return
|
||||||
}
|
}
|
||||||
|
|
||||||
err = ioutil.WriteFile(path.Join(mountPath, secret.Name), []byte(secret.Value), secretFilePermission)
|
data := secret.RawValue
|
||||||
|
if len(data) == 0 {
|
||||||
|
data = []byte(secret.Value)
|
||||||
|
}
|
||||||
|
|
||||||
|
err = ioutil.WriteFile(path.Join(mountPath, secret.Name), data, secretFilePermission)
|
||||||
|
|
||||||
if err != nil {
|
if err != nil {
|
||||||
log.Printf("[secret] error %s", err.Error())
|
log.Printf("[secret] error %s", err.Error())
|
||||||
@ -137,10 +150,6 @@ func parseSecret(r *http.Request) (types.Secret, error) {
|
|||||||
return secret, err
|
return secret, err
|
||||||
}
|
}
|
||||||
|
|
||||||
if isTraversal(secret.Name) {
|
|
||||||
return secret, fmt.Errorf(traverseErrorSt)
|
|
||||||
}
|
|
||||||
|
|
||||||
return secret, err
|
return secret, err
|
||||||
}
|
}
|
||||||
|
|
||||||
@ -150,3 +159,13 @@ func isTraversal(name string) bool {
|
|||||||
return strings.Contains(name, fmt.Sprintf("%s", string(os.PathSeparator))) ||
|
return strings.Contains(name, fmt.Sprintf("%s", string(os.PathSeparator))) ||
|
||||||
strings.Contains(name, "..")
|
strings.Contains(name, "..")
|
||||||
}
|
}
|
||||||
|
|
||||||
|
func validateSecret(secret types.Secret) error {
|
||||||
|
if strings.TrimSpace(secret.Name) == "" {
|
||||||
|
return fmt.Errorf("non-empty name is required")
|
||||||
|
}
|
||||||
|
if isTraversal(secret.Name) {
|
||||||
|
return fmt.Errorf(traverseErrorSt)
|
||||||
|
}
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|||||||
@ -1,63 +1,163 @@
|
|||||||
package handlers
|
package handlers
|
||||||
|
|
||||||
import (
|
import (
|
||||||
"bytes"
|
|
||||||
"encoding/json"
|
|
||||||
"net/http"
|
"net/http"
|
||||||
"net/http/httptest"
|
"net/http/httptest"
|
||||||
|
"os"
|
||||||
|
"path/filepath"
|
||||||
|
"reflect"
|
||||||
|
"strings"
|
||||||
"testing"
|
"testing"
|
||||||
|
|
||||||
"github.com/openfaas/faas-provider/types"
|
"github.com/openfaas/faas-provider/types"
|
||||||
)
|
)
|
||||||
|
|
||||||
func Test_parseSecretValidName(t *testing.T) {
|
func Test_parseSecret(t *testing.T) {
|
||||||
|
cases := []struct {
|
||||||
|
name string
|
||||||
|
payload string
|
||||||
|
expError string
|
||||||
|
expSecret types.Secret
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
name: "no error when name is valid without extention and with no traversal",
|
||||||
|
payload: `{"name": "authorized_keys", "value": "foo"}`,
|
||||||
|
expSecret: types.Secret{Name: "authorized_keys", Value: "foo"},
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "no error when name is valid and parses RawValue correctly",
|
||||||
|
payload: `{"name": "authorized_keys", "rawValue": "YmFy"}`,
|
||||||
|
expSecret: types.Secret{Name: "authorized_keys", RawValue: []byte("bar")},
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "no error when name is valid with dot and with no traversal",
|
||||||
|
payload: `{"name": "authorized.keys", "value": "foo"}`,
|
||||||
|
expSecret: types.Secret{Name: "authorized.keys", Value: "foo"},
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
s := types.Secret{Name: "authorized_keys"}
|
for _, tc := range cases {
|
||||||
body, _ := json.Marshal(s)
|
t.Run(tc.name, func(t *testing.T) {
|
||||||
reader := bytes.NewReader(body)
|
reader := strings.NewReader(tc.payload)
|
||||||
r := httptest.NewRequest(http.MethodPost, "/", reader)
|
r := httptest.NewRequest(http.MethodPost, "/", reader)
|
||||||
_, err := parseSecret(r)
|
secret, err := parseSecret(r)
|
||||||
|
if err != nil && tc.expError == "" {
|
||||||
|
t.Fatalf("unexpected error: %s", err)
|
||||||
|
return
|
||||||
|
}
|
||||||
|
|
||||||
|
if tc.expError != "" {
|
||||||
|
if err == nil {
|
||||||
|
t.Fatalf("expected error: %s, got nil", tc.expError)
|
||||||
|
}
|
||||||
|
if err.Error() != tc.expError {
|
||||||
|
t.Fatalf("expected error: %s, got: %s", tc.expError, err)
|
||||||
|
}
|
||||||
|
|
||||||
|
return
|
||||||
|
}
|
||||||
|
|
||||||
|
if !reflect.DeepEqual(secret, tc.expSecret) {
|
||||||
|
t.Fatalf("expected secret: %+v, got: %+v", tc.expSecret, secret)
|
||||||
|
}
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
func TestSecretCreation(t *testing.T) {
|
||||||
|
mountPath, err := os.MkdirTemp("", "test_secret_creation")
|
||||||
if err != nil {
|
if err != nil {
|
||||||
t.Fatalf("secret name is valid with no traversal characters")
|
t.Fatalf("unexpected error while creating temp directory: %s", err)
|
||||||
}
|
}
|
||||||
}
|
|
||||||
|
defer os.RemoveAll(mountPath)
|
||||||
func Test_parseSecretValidNameWithDot(t *testing.T) {
|
|
||||||
|
handler := MakeSecretHandler(nil, mountPath)
|
||||||
s := types.Secret{Name: "authorized.keys"}
|
|
||||||
body, _ := json.Marshal(s)
|
cases := []struct {
|
||||||
reader := bytes.NewReader(body)
|
name string
|
||||||
r := httptest.NewRequest(http.MethodPost, "/", reader)
|
verb string
|
||||||
_, err := parseSecret(r)
|
payload string
|
||||||
|
status int
|
||||||
if err != nil {
|
secretPath string
|
||||||
t.Fatalf("secret name is valid with no traversal characters")
|
secret string
|
||||||
}
|
err string
|
||||||
}
|
}{
|
||||||
|
{
|
||||||
func Test_parseSecretWithTraversalWithSlash(t *testing.T) {
|
name: "returns error when the name contains a traversal",
|
||||||
|
verb: http.MethodPost,
|
||||||
s := types.Secret{Name: "/root/.ssh/authorized_keys"}
|
payload: `{"name": "/root/.ssh/authorized_keys", "value": "foo"}`,
|
||||||
body, _ := json.Marshal(s)
|
status: http.StatusBadRequest,
|
||||||
reader := bytes.NewReader(body)
|
err: "directory traversal found in name\n",
|
||||||
r := httptest.NewRequest(http.MethodPost, "/", reader)
|
},
|
||||||
_, err := parseSecret(r)
|
{
|
||||||
|
name: "returns error when the name contains a traversal",
|
||||||
if err == nil {
|
verb: http.MethodPost,
|
||||||
t.Fatalf("secret name should fail due to path traversal")
|
payload: `{"name": "..", "value": "foo"}`,
|
||||||
}
|
status: http.StatusBadRequest,
|
||||||
}
|
err: "directory traversal found in name\n",
|
||||||
|
},
|
||||||
func Test_parseSecretWithTraversalWithDoubleDot(t *testing.T) {
|
{
|
||||||
|
name: "empty request returns a validation error",
|
||||||
s := types.Secret{Name: ".."}
|
verb: http.MethodPost,
|
||||||
body, _ := json.Marshal(s)
|
payload: `{}`,
|
||||||
reader := bytes.NewReader(body)
|
status: http.StatusBadRequest,
|
||||||
r := httptest.NewRequest(http.MethodPost, "/", reader)
|
err: "non-empty name is required\n",
|
||||||
_, err := parseSecret(r)
|
},
|
||||||
|
{
|
||||||
if err == nil {
|
name: "can create secret from string",
|
||||||
t.Fatalf("secret name should fail due to path traversal")
|
verb: http.MethodPost,
|
||||||
|
payload: `{"name": "foo", "value": "bar"}`,
|
||||||
|
status: http.StatusOK,
|
||||||
|
secretPath: "/openfaas-fn/foo",
|
||||||
|
secret: "bar",
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "can create secret from raw value",
|
||||||
|
verb: http.MethodPost,
|
||||||
|
payload: `{"name": "foo", "rawValue": "YmFy"}`,
|
||||||
|
status: http.StatusOK,
|
||||||
|
secretPath: "/openfaas-fn/foo",
|
||||||
|
secret: "bar",
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "can create secret in non-default namespace from raw value",
|
||||||
|
verb: http.MethodPost,
|
||||||
|
payload: `{"name": "pity", "rawValue": "dGhlIGZvbw==", "namespace": "a-team"}`,
|
||||||
|
status: http.StatusOK,
|
||||||
|
secretPath: "/a-team/pity",
|
||||||
|
secret: "the foo",
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tc := range cases {
|
||||||
|
t.Run(tc.name, func(t *testing.T) {
|
||||||
|
req := httptest.NewRequest(tc.verb, "http://example.com/foo", strings.NewReader(tc.payload))
|
||||||
|
w := httptest.NewRecorder()
|
||||||
|
|
||||||
|
handler(w, req)
|
||||||
|
|
||||||
|
resp := w.Result()
|
||||||
|
if resp.StatusCode != tc.status {
|
||||||
|
t.Logf("response body: %s", w.Body.String())
|
||||||
|
t.Fatalf("expected status: %d, got: %d", tc.status, resp.StatusCode)
|
||||||
|
}
|
||||||
|
|
||||||
|
if resp.StatusCode != http.StatusOK && w.Body.String() != tc.err {
|
||||||
|
t.Fatalf("expected error message: %q, got %q", tc.err, w.Body.String())
|
||||||
|
|
||||||
|
}
|
||||||
|
|
||||||
|
if tc.secretPath != "" {
|
||||||
|
data, err := os.ReadFile(filepath.Join(mountPath, tc.secretPath))
|
||||||
|
if err != nil {
|
||||||
|
t.Fatalf("can not read the secret from disk: %s", err)
|
||||||
|
}
|
||||||
|
|
||||||
|
if string(data) != tc.secret {
|
||||||
|
t.Fatalf("expected secret value: %s, got %s", tc.secret, string(data))
|
||||||
|
}
|
||||||
|
}
|
||||||
|
})
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|||||||
@ -8,6 +8,8 @@ import (
|
|||||||
"os"
|
"os"
|
||||||
"path"
|
"path"
|
||||||
"sort"
|
"sort"
|
||||||
|
"strconv"
|
||||||
|
"strings"
|
||||||
|
|
||||||
"github.com/alexellis/k3sup/pkg/env"
|
"github.com/alexellis/k3sup/pkg/env"
|
||||||
"github.com/compose-spec/compose-go/loader"
|
"github.com/compose-spec/compose-go/loader"
|
||||||
@ -26,7 +28,8 @@ import (
|
|||||||
)
|
)
|
||||||
|
|
||||||
const (
|
const (
|
||||||
workingDirectoryPermission = 0644
|
// workingDirectoryPermission user read/write/execute, group and others: read-only
|
||||||
|
workingDirectoryPermission = 0744
|
||||||
)
|
)
|
||||||
|
|
||||||
type Service struct {
|
type Service struct {
|
||||||
@ -145,6 +148,28 @@ func (s *Supervisor) Start(svcs []Service) error {
|
|||||||
Type: "bind",
|
Type: "bind",
|
||||||
Options: []string{"rbind", "rw"},
|
Options: []string{"rbind", "rw"},
|
||||||
})
|
})
|
||||||
|
|
||||||
|
// Only create directories, not files.
|
||||||
|
// Some files don't have a suffix, such as secrets.
|
||||||
|
if len(path.Ext(mnt.Src)) == 0 &&
|
||||||
|
!strings.HasPrefix(mnt.Src, "/var/lib/faasd/secrets/") {
|
||||||
|
// src is already prefixed with wd from an earlier step
|
||||||
|
src := mnt.Src
|
||||||
|
fmt.Printf("Creating local directory: %s\n", src)
|
||||||
|
if err := os.MkdirAll(src, workingDirectoryPermission); err != nil {
|
||||||
|
if !errors.Is(os.ErrExist, err) {
|
||||||
|
fmt.Printf("Unable to create: %s, %s\n", src, err)
|
||||||
|
}
|
||||||
|
}
|
||||||
|
if len(svc.User) > 0 {
|
||||||
|
uid, err := strconv.Atoi(svc.User)
|
||||||
|
if err == nil {
|
||||||
|
if err := os.Chown(src, uid, -1); err != nil {
|
||||||
|
fmt.Printf("Unable to chown: %s to %d, error: %s\n", src, uid, err)
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|||||||
Reference in New Issue
Block a user