mirror of
https://github.com/openfaas/faasd.git
synced 2025-06-21 14:23:34 +00:00
Compare commits
2 Commits
0.15.0-rc2
...
wait-for-h
| Author | SHA1 | Date | |
|---|---|---|---|
| bbd3b4ff07 | |||
| 1d07fda0a4 |
4
.github/ISSUE_TEMPLATE.md
vendored
4
.github/ISSUE_TEMPLATE.md
vendored
@ -1,7 +1,3 @@
|
||||
## Due diligence
|
||||
|
||||
Before you for help or support, make sure that you've [consulted the faasd manual "Serverless For Everyone Else"](https://openfaas.gumroad.com/l/serverless-for-everyone-else).
|
||||
|
||||
<!--- Provide a general summary of the issue in the Title above -->
|
||||
|
||||
## Expected Behaviour
|
||||
|
||||
2
.github/workflows/build.yaml
vendored
2
.github/workflows/build.yaml
vendored
@ -12,7 +12,7 @@ jobs:
|
||||
GO111MODULE: off
|
||||
strategy:
|
||||
matrix:
|
||||
go-version: [1.17.x]
|
||||
go-version: [1.16.x]
|
||||
os: [ubuntu-latest]
|
||||
runs-on: ${{ matrix.os }}
|
||||
steps:
|
||||
|
||||
2
.github/workflows/publish.yaml
vendored
2
.github/workflows/publish.yaml
vendored
@ -9,7 +9,7 @@ jobs:
|
||||
publish:
|
||||
strategy:
|
||||
matrix:
|
||||
go-version: [ 1.17.x ]
|
||||
go-version: [ 1.16.x ]
|
||||
os: [ ubuntu-latest ]
|
||||
runs-on: ${{ matrix.os }}
|
||||
steps:
|
||||
|
||||
@ -45,7 +45,7 @@ Additional resources:
|
||||
|
||||
Most importantly, it's easy to manage so you can set it up and leave it alone to run your functions.
|
||||
|
||||
[](https://www.youtube.com/watch?v=WX1tZoSXy8E)
|
||||
|
||||
|
||||
> Demo of faasd running asynchronous functions
|
||||
|
||||
@ -167,6 +167,4 @@ For completed features, WIP and upcoming roadmap see:
|
||||
|
||||
See [ROADMAP.md](docs/ROADMAP.md)
|
||||
|
||||
Want to build a patch without setting up a complete development environment? See [docs/PATCHES.md](docs/PATCHES.md)
|
||||
|
||||
Are you looking to hack on faasd? Follow the [developer instructions](docs/DEV.md) for a manual installation, or use the `hack/install.sh` script and pick up from there.
|
||||
|
||||
@ -10,7 +10,17 @@ packages:
|
||||
- git
|
||||
|
||||
runcmd:
|
||||
- curl -sfL https://raw.githubusercontent.com/openfaas/faasd/master/hack/install.sh | sh -s -
|
||||
- curl -sLSf https://github.com/containerd/containerd/releases/download/v1.5.4/containerd-1.5.4-linux-amd64.tar.gz > /tmp/containerd.tar.gz && tar -xvf /tmp/containerd.tar.gz -C /usr/local/bin/ --strip-components=1
|
||||
- curl -SLfs https://raw.githubusercontent.com/containerd/containerd/v1.5.4/containerd.service | tee /etc/systemd/system/containerd.service
|
||||
- systemctl daemon-reload && systemctl start containerd
|
||||
- systemctl enable containerd
|
||||
- /sbin/sysctl -w net.ipv4.conf.all.forwarding=1
|
||||
- mkdir -p /opt/cni/bin
|
||||
- curl -sSL https://github.com/containernetworking/plugins/releases/download/v0.8.5/cni-plugins-linux-amd64-v0.8.5.tgz | tar -xz -C /opt/cni/bin
|
||||
- mkdir -p /go/src/github.com/openfaas/
|
||||
- cd /go/src/github.com/openfaas/ && git clone --depth 1 --branch 0.13.0 https://github.com/openfaas/faasd
|
||||
- curl -fSLs "https://github.com/openfaas/faasd/releases/download/0.13.0/faasd" --output "/usr/local/bin/faasd" && chmod a+x "/usr/local/bin/faasd"
|
||||
- cd /go/src/github.com/openfaas/faasd/ && /usr/local/bin/faasd install
|
||||
- systemctl status -l containerd --no-pager
|
||||
- journalctl -u faasd-provider --no-pager
|
||||
- systemctl status -l faasd-provider --no-pager
|
||||
|
||||
@ -98,12 +98,12 @@ func makeProviderCmd() *cobra.Command {
|
||||
DeployHandler: handlers.MakeDeployHandler(client, cni, baseUserSecretsPath, alwaysPull),
|
||||
FunctionReader: handlers.MakeReadHandler(client),
|
||||
ReplicaReader: handlers.MakeReplicaReaderHandler(client),
|
||||
ReplicaUpdater: handlers.MakeReplicaUpdateHandler(client, cni),
|
||||
ReplicaUpdater: handlers.MakeReplicaUpdateHandler(client, cni, invokeResolver),
|
||||
UpdateHandler: handlers.MakeUpdateHandler(client, cni, baseUserSecretsPath, alwaysPull),
|
||||
HealthHandler: func(w http.ResponseWriter, r *http.Request) {},
|
||||
InfoHandler: handlers.MakeInfoHandler(Version, GitCommit),
|
||||
ListNamespaceHandler: handlers.MakeNamespacesLister(client),
|
||||
SecretHandler: handlers.MakeSecretHandler(client.NamespaceService(), baseUserSecretsPath),
|
||||
SecretHandler: handlers.MakeSecretHandler(client, baseUserSecretsPath),
|
||||
LogHandler: logs.NewLogHandlerFunc(faasdlogs.New(), config.ReadTimeout),
|
||||
}
|
||||
|
||||
|
||||
@ -20,43 +20,28 @@ services:
|
||||
|
||||
nats:
|
||||
image: docker.io/library/nats-streaming:0.22.0
|
||||
# nobody
|
||||
user: "65534"
|
||||
command:
|
||||
- "/nats-streaming-server"
|
||||
- "-m"
|
||||
- "8222"
|
||||
- "--store=file"
|
||||
- "--dir=/nats"
|
||||
- "--store=memory"
|
||||
- "--cluster_id=faas-cluster"
|
||||
volumes:
|
||||
# Data directory
|
||||
- type: bind
|
||||
source: ./nats
|
||||
target: /nats
|
||||
# ports:
|
||||
# - "127.0.0.1:8222:8222"
|
||||
|
||||
prometheus:
|
||||
image: docker.io/prom/prometheus:v2.14.0
|
||||
# nobody
|
||||
user: "65534"
|
||||
volumes:
|
||||
# Config directory
|
||||
- type: bind
|
||||
source: ./prometheus.yml
|
||||
target: /etc/prometheus/prometheus.yml
|
||||
# Data directory
|
||||
- type: bind
|
||||
source: ./prometheus
|
||||
target: /prometheus
|
||||
cap_add:
|
||||
- CAP_NET_RAW
|
||||
ports:
|
||||
- "127.0.0.1:9090:9090"
|
||||
|
||||
gateway:
|
||||
image: ghcr.io/openfaas/gateway:0.21.3
|
||||
image: ghcr.io/openfaas/gateway:0.21.0
|
||||
environment:
|
||||
- basic_auth=true
|
||||
- functions_provider_url=http://faasd-provider:8081/
|
||||
|
||||
@ -1,11 +1,7 @@
|
||||
## Instructions for building and testing faasd locally
|
||||
## Instructions for hacking on faasd itself
|
||||
|
||||
> Note: if you're just wanting to try out faasd, then it's likely that you're on the wrong page. This is a detailed set of instructions for those wanting to contribute or customise faasd. Feel free to go back to the homepage and pick a tutorial instead.
|
||||
|
||||
Do you want to help the community test a pull request?
|
||||
|
||||
See these instructions instead: [Testing patches](/docs/PATCHES.md)
|
||||
|
||||
### Pre-reqs
|
||||
|
||||
> It's recommended that you do not install Docker on the same host as faasd, since 1) they may both use different versions of containerd and 2) docker's networking rules can disrupt faasd's networking. When using faasd - make your faasd server a faasd server, and build container image on your laptop or in a CI pipeline.
|
||||
|
||||
@ -27,112 +27,111 @@ It took me about 2-3 minutes to run through everything after installing multipas
|
||||
|
||||
* Get my cloud-config.txt file
|
||||
|
||||
```sh
|
||||
curl -sSLO https://raw.githubusercontent.com/openfaas/faasd/master/cloud-config.txt
|
||||
```
|
||||
```sh
|
||||
curl -sSLO https://raw.githubusercontent.com/openfaas/faasd/master/cloud-config.txt
|
||||
```
|
||||
|
||||
* Boot the VM
|
||||
* Update the SSH key to match your own, edit `cloud-config.txt`:
|
||||
|
||||
The `cloud-config.txt` contains an ssh key to allow your local machine to access the VM. However, this must be updated with your local ssh key.
|
||||
This command will update the key with your local public key value and start the VM.
|
||||
Replace the 2nd line with the contents of `~/.ssh/id_rsa.pub`:
|
||||
|
||||
```sh
|
||||
sed "s/ssh-rsa.*/$(cat $HOME/.ssh/id_*.pub)/" cloud-config.txt | multipass launch --name faasd --cloud-init -
|
||||
```
|
||||
```
|
||||
ssh_authorized_keys:
|
||||
- ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC8Q/aUYUr3P1XKVucnO9mlWxOjJm+K01lHJR90MkHC9zbfTqlp8P7C3J26zKAuzHXOeF+VFxETRr6YedQKW9zp5oP7sN+F2gr/pO7GV3VmOqHMV7uKfyUQfq7H1aVzLfCcI7FwN2Zekv3yB7kj35pbsMa1Za58aF6oHRctZU6UWgXXbRxP+B04DoVU7jTstQ4GMoOCaqYhgPHyjEAS3DW0kkPW6HzsvJHkxvVcVlZ/wNJa1Ie/yGpzOzWIN0Ol0t2QT/RSWOhfzO1A2P0XbPuZ04NmriBonO9zR7T1fMNmmtTuK7WazKjQT3inmYRAqU6pe8wfX8WIWNV7OowUjUsv alex@alexr.local
|
||||
```
|
||||
|
||||
This can also be done manually, just replace the 2nd line of the `cloud-config.txt` with the coPntents of your public ssh key, usually either `~/.ssh/id_rsa.pub` or `~/.ssh/id_ed25519.pub`
|
||||
* Boot the VM
|
||||
|
||||
```
|
||||
ssh_authorized_keys:
|
||||
- ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC8Q/aUYUr3P1XKVucnO9mlWxOjJm+K01lHJR90MkHC9zbfTqlp8P7C3J26zKAuzHXOeF+VFxETRr6YedQKW9zp5oP7sN+F2gr/pO7GV3VmOqHMV7uKfyUQfq7H1aVzLfCcI7FwN2Zekv3yB7kj35pbsMa1Za58aF6oHRctZU6UWgXXbRxP+B04DoVU7jTstQ4GMoOCaqYhgPHyjEAS3DW0kkPW6HzsvJHkxvVcVlZ/wNJa1Ie/yGpzOzWIN0Ol0t2QT/RSWOhfzO1A2P0XbPuZ04NmriBonO9zR7T1fMNmmtTuK7WazKjQT3inmYRAqU6pe8wfX8WIWNV7OowUjUsv alex@alexr.local
|
||||
```
|
||||
```sh
|
||||
multipass launch --cloud-init cloud-config.txt --name faasd
|
||||
```
|
||||
|
||||
* Get the VM's IP and connect with `ssh`
|
||||
|
||||
```sh
|
||||
multipass info faasd
|
||||
Name: faasd
|
||||
State: Running
|
||||
IPv4: 192.168.64.14
|
||||
Release: Ubuntu 18.04.3 LTS
|
||||
Image hash: a720c34066dc (Ubuntu 18.04 LTS)
|
||||
Load: 0.79 0.19 0.06
|
||||
Disk usage: 1.1G out of 4.7G
|
||||
Memory usage: 145.6M out of 985.7M
|
||||
```
|
||||
```sh
|
||||
multipass info faasd
|
||||
Name: faasd
|
||||
State: Running
|
||||
IPv4: 192.168.64.14
|
||||
Release: Ubuntu 18.04.3 LTS
|
||||
Image hash: a720c34066dc (Ubuntu 18.04 LTS)
|
||||
Load: 0.79 0.19 0.06
|
||||
Disk usage: 1.1G out of 4.7G
|
||||
Memory usage: 145.6M out of 985.7M
|
||||
```
|
||||
|
||||
Set the variable `IP`:
|
||||
Set the variable `IP`:
|
||||
|
||||
```
|
||||
export IP="192.168.64.14"
|
||||
```
|
||||
```
|
||||
export IP="192.168.64.14"
|
||||
```
|
||||
|
||||
You can also try to use `jq` to get the IP into a variable:
|
||||
You can also try to use `jq` to get the IP into a variable:
|
||||
|
||||
```sh
|
||||
export IP=$(multipass info faasd --format json| jq -r '.info.faasd.ipv4[0]')
|
||||
```
|
||||
```sh
|
||||
export IP=$(multipass info faasd --format json| jq -r '.info.faasd.ipv4[0]')
|
||||
```
|
||||
|
||||
Connect to the IP listed:
|
||||
Connect to the IP listed:
|
||||
|
||||
```sh
|
||||
ssh ubuntu@$IP
|
||||
```
|
||||
```sh
|
||||
ssh ubuntu@$IP
|
||||
```
|
||||
|
||||
Log out once you know it works.
|
||||
Log out once you know it works.
|
||||
|
||||
* Let's capture the authentication password into a file for use with `faas-cli`
|
||||
|
||||
```
|
||||
ssh ubuntu@$IP "sudo cat /var/lib/faasd/secrets/basic-auth-password" > basic-auth-password
|
||||
```
|
||||
```
|
||||
ssh ubuntu@$IP "sudo cat /var/lib/faasd/secrets/basic-auth-password" > basic-auth-password
|
||||
```
|
||||
|
||||
## Try faasd (OpenFaaS)
|
||||
|
||||
* Login from your laptop (the host)
|
||||
|
||||
```
|
||||
export OPENFAAS_URL=http://$IP:8080
|
||||
cat basic-auth-password | faas-cli login -s
|
||||
```
|
||||
```
|
||||
export OPENFAAS_URL=http://$IP:8080
|
||||
cat basic-auth-password | faas-cli login -s
|
||||
```
|
||||
|
||||
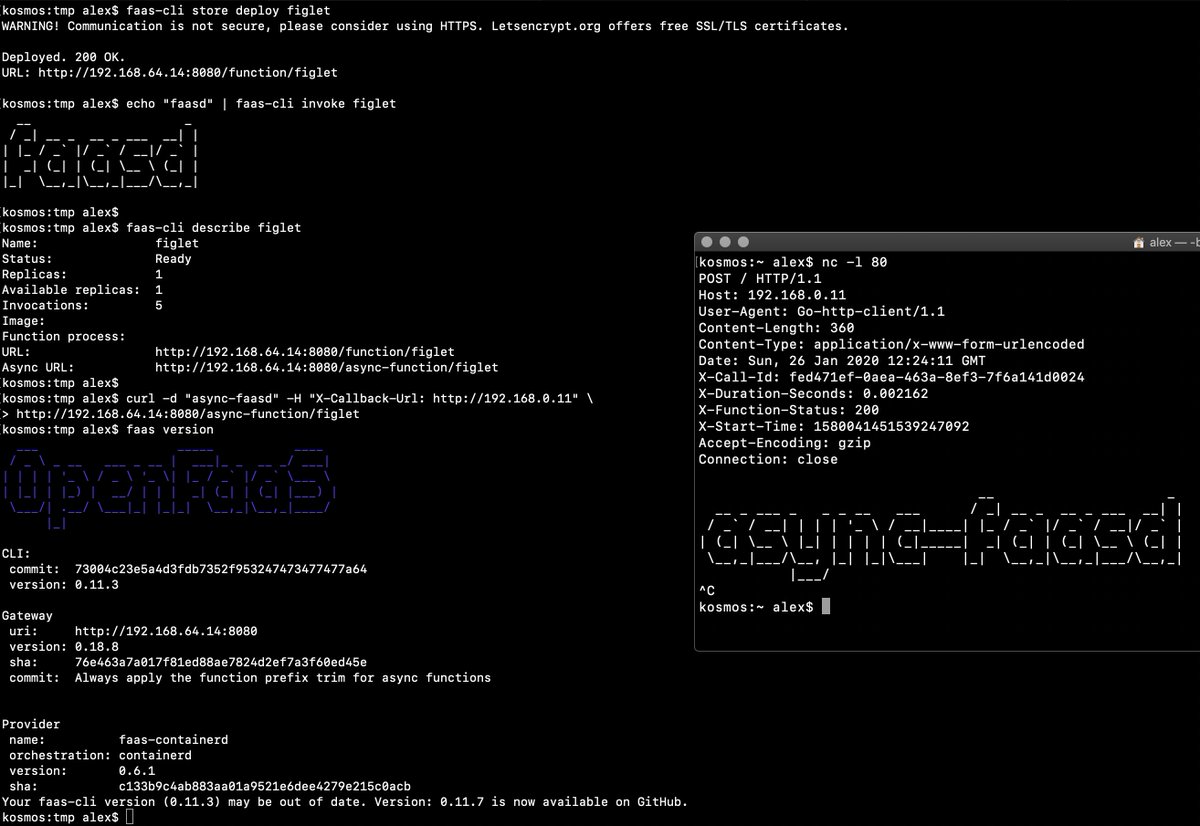
* Deploy a function and invoke it
|
||||
|
||||
```
|
||||
faas-cli store deploy figlet --env write_timeout=1s
|
||||
echo "faasd" | faas-cli invoke figlet
|
||||
```
|
||||
faas-cli store deploy figlet --env write_timeout=1s
|
||||
echo "faasd" | faas-cli invoke figlet
|
||||
|
||||
faas-cli describe figlet
|
||||
faas-cli describe figlet
|
||||
|
||||
# Run async
|
||||
curl -i -d "faasd-async" $OPENFAAS_URL/async-function/figlet
|
||||
# Run async
|
||||
curl -i -d "faasd-async" $OPENFAAS_URL/async-function/figlet
|
||||
|
||||
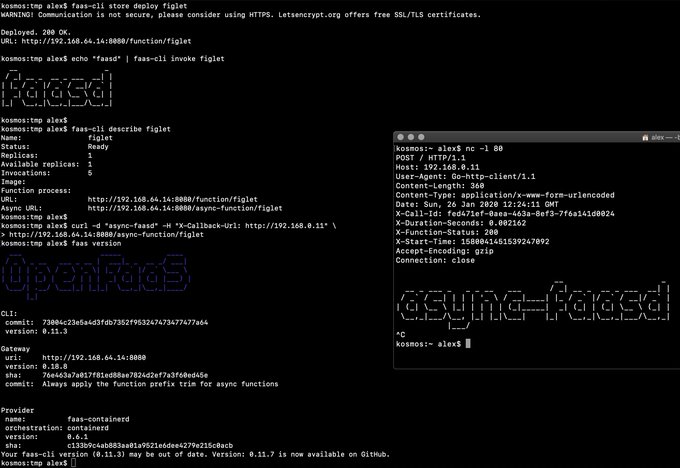
# Run async with a callback
|
||||
# Run async with a callback
|
||||
|
||||
curl -i -d "faasd-async" -H "X-Callback-Url: http://some-request-bin.com/path" $OPENFAAS_URL/async-function/figlet
|
||||
```
|
||||
curl -i -d "faasd-async" -H "X-Callback-Url: http://some-request-bin.com/path" $OPENFAAS_URL/async-function/figlet
|
||||
```
|
||||
|
||||
You can also checkout the other store functions: `faas-cli store list`
|
||||
You can also checkout the other store functions: `faas-cli store list`
|
||||
|
||||
* Try the UI
|
||||
|
||||
Head over to the UI from your laptop and remember that your password is in the `basic-auth-password` file. The username is `admin`:
|
||||
Head over to the UI from your laptop and remember that your password is in the `basic-auth-password` file. The username is `admin`:
|
||||
|
||||
```
|
||||
echo http://$IP:8080
|
||||
```
|
||||
```
|
||||
echo http://$IP:8080
|
||||
```
|
||||
|
||||
* Stop/start the instance
|
||||
|
||||
```sh
|
||||
multipass stop faasd
|
||||
```
|
||||
```sh
|
||||
multipass stop faasd
|
||||
```
|
||||
|
||||
* Delete, if you want to:
|
||||
|
||||
```
|
||||
multipass delete --purge faasd
|
||||
```
|
||||
```
|
||||
multipass delete --purge faasd
|
||||
```
|
||||
|
||||
You now have a faasd appliance on your Mac. You can also use this cloud-init file with public cloud like AWS or DigitalOcean.
|
||||
|
||||
|
||||
@ -1,88 +0,0 @@
|
||||
## Instructions for testing a patch for faasd
|
||||
|
||||
### Launch a virtual machine
|
||||
|
||||
You can use any kind of Linux virtual machine, Ubuntu 20.04 is recommended.
|
||||
|
||||
Launch a cloud VM or use [Multipass](https://multipass.run), which is free to use an can be run locally. A Raspberry Pi 3 or 4 could also be used, but will need you to run `make dist` to cross compile a valid binary.
|
||||
|
||||
### Copy over your SSH key
|
||||
|
||||
Your SSH key will be used, so that you can copy a new faasd binary over to the host.
|
||||
|
||||
```bash
|
||||
multipass launch \
|
||||
--mem 4G \
|
||||
-c 2 \
|
||||
-n faasd
|
||||
|
||||
# Then access its shell
|
||||
multipass shell faasd
|
||||
|
||||
# Edit .ssh/authorized_keys
|
||||
|
||||
# Add .ssh/id_rsa.pub from your host and save the file
|
||||
```
|
||||
|
||||
### Install faasd on the VM
|
||||
|
||||
You start off with the upstream version of faasd on the host, then add the new version over the top later on.
|
||||
|
||||
```bash
|
||||
cd /tmp/
|
||||
git clone https://github.com/openfaas/faasd --depth=1
|
||||
cd faasd/hack
|
||||
./install.sh
|
||||
|
||||
# Run the login command given to you at the end of the script
|
||||
```
|
||||
|
||||
Get the multipass IP address:
|
||||
|
||||
```bash
|
||||
export IP=$(multipass info faasd --format json| jq -r '.info.faasd.ipv4[0]')
|
||||
```
|
||||
|
||||
### Build a new faasd binary with the patch
|
||||
|
||||
Check out faasd on your local computer
|
||||
|
||||
```bash
|
||||
git clone https://github.com/openfaas/faasd
|
||||
cd faasd
|
||||
|
||||
gh pr checkout #PR_NUMBER_HERE
|
||||
|
||||
GOOS=linux go build
|
||||
|
||||
# You can also run "make dist" which is slower, but includes
|
||||
# a version and binaries for other platforms such as the Raspberry Pi
|
||||
```
|
||||
|
||||
### Copy it over to the VM
|
||||
|
||||
Now build a new faasd binary and copy it to the VM:
|
||||
|
||||
```bash
|
||||
scp faasd ubuntu@$IP:~/
|
||||
```
|
||||
|
||||
Now deploy the new version on the VM:
|
||||
|
||||
```bash
|
||||
killall -9 faasd-linux; killall -9 faasd-linux ; mv ./faasd-linux /usr/local/bin/faasd
|
||||
```
|
||||
|
||||
### Check it worked and test that patch
|
||||
|
||||
Now run a command with `faas-cli` such as:
|
||||
|
||||
* `faas-cli list`
|
||||
* `faas-cli version`
|
||||
|
||||
See the testing instructions on the PR and run through those steps.
|
||||
|
||||
Post your results on GitHub to assist the creator of the pull request.
|
||||
|
||||
You can see how to get the logs for various components using the [eBook Serverless For Everyone Else](https://gumroad.com/l/serverless-for-everyone-else), or by consulting the [DEV.md](/docs/DEV.md) guide.
|
||||
|
||||
@ -75,10 +75,10 @@ sudo systemctl restart faasd
|
||||
|
||||
Should have:
|
||||
|
||||
* [ ] Offer a recommendation or implement a strategy for faasd replication/HA
|
||||
* [ ] Resolve core services from functions by populating/sharing `/etc/hosts` between `faasd` and `faasd-provider`
|
||||
* [ ] Docs or examples on how to use the various connectors and connector-sdk
|
||||
* [ ] Monitor and restart any of the core components at runtime if the container stops
|
||||
* [ ] Asynchronous function deletion instead of synchronous
|
||||
* [ ] Asynchronous function start-up instead of synchronous
|
||||
* [ ] Asynchronous deletion instead of synchronous
|
||||
|
||||
Nice to Have:
|
||||
|
||||
@ -89,8 +89,6 @@ Nice to Have:
|
||||
|
||||
### Completed
|
||||
|
||||
* [x] Docs or examples on how to use the various event connectors (Yes in the eBook)
|
||||
* [x] Resolve core services from functions by populating/sharing `/etc/hosts` between `faasd` and `faasd-provider`
|
||||
* [x] Provide a cloud-init configuration for faasd bootstrap
|
||||
* [x] Configure core services from a docker-compose.yaml file
|
||||
* [x] Store and fetch logs from the journal
|
||||
|
||||
@ -43,7 +43,7 @@ func MakeDeleteHandler(client *containerd.Client, cni gocni.CNI) func(w http.Res
|
||||
lookupNamespace := getRequestNamespace(readNamespaceFromQuery(r))
|
||||
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), lookupNamespace)
|
||||
valid, err := validNamespace(client, lookupNamespace)
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
|
||||
@ -54,7 +54,7 @@ func MakeDeployHandler(client *containerd.Client, cni gocni.CNI, secretMountPath
|
||||
namespace := getRequestNamespace(req.Namespace)
|
||||
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), namespace)
|
||||
valid, err := validNamespace(client, namespace)
|
||||
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
|
||||
@ -37,7 +37,7 @@ type Function struct {
|
||||
func ListFunctions(client *containerd.Client, namespace string) (map[string]*Function, error) {
|
||||
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), namespace)
|
||||
valid, err := validNamespace(client, namespace)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
@ -2,11 +2,10 @@ package handlers
|
||||
|
||||
import (
|
||||
"encoding/json"
|
||||
"k8s.io/apimachinery/pkg/api/resource"
|
||||
"log"
|
||||
"net/http"
|
||||
|
||||
"k8s.io/apimachinery/pkg/api/resource"
|
||||
|
||||
"github.com/containerd/containerd"
|
||||
"github.com/openfaas/faas-provider/types"
|
||||
)
|
||||
@ -17,7 +16,7 @@ func MakeReadHandler(client *containerd.Client) func(w http.ResponseWriter, r *h
|
||||
|
||||
lookupNamespace := getRequestNamespace(readNamespaceFromQuery(r))
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), lookupNamespace)
|
||||
valid, err := validNamespace(client, lookupNamespace)
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
@ -40,7 +39,7 @@ func MakeReadHandler(client *containerd.Client) func(w http.ResponseWriter, r *h
|
||||
annotations := &fn.annotations
|
||||
labels := &fn.labels
|
||||
memory := resource.NewQuantity(fn.memoryLimit, resource.BinarySI)
|
||||
status := types.FunctionStatus{
|
||||
res = append(res, types.FunctionStatus{
|
||||
Name: fn.name,
|
||||
Image: fn.image,
|
||||
Replicas: uint64(fn.replicas),
|
||||
@ -50,17 +49,9 @@ func MakeReadHandler(client *containerd.Client) func(w http.ResponseWriter, r *h
|
||||
Secrets: fn.secrets,
|
||||
EnvVars: fn.envVars,
|
||||
EnvProcess: fn.envProcess,
|
||||
Limits: &types.FunctionResources{Memory: memory.String()},
|
||||
CreatedAt: fn.createdAt,
|
||||
}
|
||||
|
||||
// Do not remove below memory check for 0
|
||||
// Memory limit should not be included in status until set explicitly
|
||||
limit := &types.FunctionResources{Memory: memory.String()}
|
||||
if limit.Memory != "0" {
|
||||
status.Limits = limit
|
||||
}
|
||||
|
||||
res = append(res, status)
|
||||
})
|
||||
}
|
||||
|
||||
body, _ := json.Marshal(res)
|
||||
|
||||
@ -17,7 +17,7 @@ func MakeReplicaReaderHandler(client *containerd.Client) func(w http.ResponseWri
|
||||
lookupNamespace := getRequestNamespace(readNamespaceFromQuery(r))
|
||||
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), lookupNamespace)
|
||||
valid, err := validNamespace(client, lookupNamespace)
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
|
||||
@ -6,16 +6,20 @@ import (
|
||||
"fmt"
|
||||
"io/ioutil"
|
||||
"log"
|
||||
"net"
|
||||
"net/http"
|
||||
"net/url"
|
||||
"time"
|
||||
|
||||
"github.com/containerd/containerd"
|
||||
"github.com/containerd/containerd/namespaces"
|
||||
gocni "github.com/containerd/go-cni"
|
||||
|
||||
"github.com/openfaas/faas-provider/proxy"
|
||||
"github.com/openfaas/faas-provider/types"
|
||||
)
|
||||
|
||||
func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI) func(w http.ResponseWriter, r *http.Request) {
|
||||
func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI, resolver proxy.BaseURLResolver) func(w http.ResponseWriter, r *http.Request) {
|
||||
|
||||
return func(w http.ResponseWriter, r *http.Request) {
|
||||
|
||||
@ -30,19 +34,16 @@ func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI) func(w h
|
||||
log.Printf("[Scale] request: %s\n", string(body))
|
||||
|
||||
req := types.ScaleServiceRequest{}
|
||||
err := json.Unmarshal(body, &req)
|
||||
|
||||
if err != nil {
|
||||
if err := json.Unmarshal(body, &req); err != nil {
|
||||
log.Printf("[Scale] error parsing input: %s\n", err)
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
|
||||
return
|
||||
}
|
||||
|
||||
namespace := getRequestNamespace(readNamespaceFromQuery(r))
|
||||
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), namespace)
|
||||
valid, err := validNamespace(client, namespace)
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
@ -55,18 +56,23 @@ func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI) func(w h
|
||||
|
||||
name := req.ServiceName
|
||||
|
||||
if _, err := GetFunction(client, name, namespace); err != nil {
|
||||
fn, err := GetFunction(client, name, namespace)
|
||||
if err != nil {
|
||||
msg := fmt.Sprintf("service %s not found", name)
|
||||
log.Printf("[Scale] %s\n", msg)
|
||||
http.Error(w, msg, http.StatusNotFound)
|
||||
return
|
||||
}
|
||||
|
||||
ctx := namespaces.WithNamespace(context.Background(), namespace)
|
||||
healthPath := "/_/healthz"
|
||||
if v := fn.annotations["com.openfaas.health.http.path"]; len(v) > 0 {
|
||||
healthPath = v
|
||||
}
|
||||
|
||||
ctr, ctrErr := client.LoadContainer(ctx, name)
|
||||
if ctrErr != nil {
|
||||
msg := fmt.Sprintf("cannot load service %s, error: %s", name, ctrErr)
|
||||
ctx := namespaces.WithNamespace(context.Background(), namespace)
|
||||
ctr, err := client.LoadContainer(ctx, name)
|
||||
if err != nil {
|
||||
msg := fmt.Sprintf("cannot load service %s, error: %s", name, err)
|
||||
log.Printf("[Scale] %s\n", msg)
|
||||
http.Error(w, msg, http.StatusNotFound)
|
||||
return
|
||||
@ -75,16 +81,16 @@ func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI) func(w h
|
||||
var taskExists bool
|
||||
var taskStatus *containerd.Status
|
||||
|
||||
task, taskErr := ctr.Task(ctx, nil)
|
||||
if taskErr != nil {
|
||||
msg := fmt.Sprintf("cannot load task for service %s, error: %s", name, taskErr)
|
||||
task, err := ctr.Task(ctx, nil)
|
||||
if err != nil {
|
||||
msg := fmt.Sprintf("cannot load task for service %s, error: %s", name, err)
|
||||
log.Printf("[Scale] %s\n", msg)
|
||||
taskExists = false
|
||||
} else {
|
||||
taskExists = true
|
||||
status, statusErr := task.Status(ctx)
|
||||
if statusErr != nil {
|
||||
msg := fmt.Sprintf("cannot load task status for %s, error: %s", name, statusErr)
|
||||
status, err := task.Status(ctx)
|
||||
if err != nil {
|
||||
msg := fmt.Sprintf("cannot load task status for %s, error: %s", name, err)
|
||||
log.Printf("[Scale] %s\n", msg)
|
||||
http.Error(w, msg, http.StatusInternalServerError)
|
||||
return
|
||||
@ -99,28 +105,31 @@ func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI) func(w h
|
||||
if req.Replicas == 0 {
|
||||
// If a task is running, pause it
|
||||
if taskExists && taskStatus.Status == containerd.Running {
|
||||
if pauseErr := task.Pause(ctx); pauseErr != nil {
|
||||
wrappedPauseErr := fmt.Errorf("error pausing task %s, error: %s", name, pauseErr)
|
||||
log.Printf("[Scale] %s\n", wrappedPauseErr.Error())
|
||||
http.Error(w, wrappedPauseErr.Error(), http.StatusNotFound)
|
||||
if err := task.Pause(ctx); err != nil {
|
||||
werr := fmt.Errorf("error pausing task %s, error: %s", name, err)
|
||||
log.Printf("[Scale] %s\n", werr.Error())
|
||||
http.Error(w, werr.Error(), http.StatusNotFound)
|
||||
return
|
||||
}
|
||||
}
|
||||
|
||||
// Otherwise, no action is required
|
||||
return
|
||||
}
|
||||
|
||||
if taskExists {
|
||||
if taskStatus != nil {
|
||||
if taskStatus.Status == containerd.Paused {
|
||||
if resumeErr := task.Resume(ctx); resumeErr != nil {
|
||||
log.Printf("[Scale] error resuming task %s, error: %s\n", name, resumeErr)
|
||||
http.Error(w, resumeErr.Error(), http.StatusBadRequest)
|
||||
if err := task.Resume(ctx); err != nil {
|
||||
log.Printf("[Scale] error resuming task %s, error: %s\n", name, err)
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
}
|
||||
} else if taskStatus.Status == containerd.Stopped {
|
||||
// Stopped tasks cannot be restarted, must be removed, and created again
|
||||
if _, delErr := task.Delete(ctx); delErr != nil {
|
||||
log.Printf("[Scale] error deleting stopped task %s, error: %s\n", name, delErr)
|
||||
http.Error(w, delErr.Error(), http.StatusBadRequest)
|
||||
if _, err := task.Delete(ctx); err != nil {
|
||||
log.Printf("[Scale] error deleting stopped task %s, error: %s\n", name, err)
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
}
|
||||
createNewTask = true
|
||||
@ -131,12 +140,70 @@ func MakeReplicaUpdateHandler(client *containerd.Client, cni gocni.CNI) func(w h
|
||||
}
|
||||
|
||||
if createNewTask {
|
||||
deployErr := createTask(ctx, client, ctr, cni)
|
||||
if deployErr != nil {
|
||||
log.Printf("[Scale] error deploying %s, error: %s\n", name, deployErr)
|
||||
http.Error(w, deployErr.Error(), http.StatusBadRequest)
|
||||
err := createTask(ctx, client, ctr, cni)
|
||||
if err != nil {
|
||||
log.Printf("[Scale] error deploying %s, error: %s\n", name, err)
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
}
|
||||
}
|
||||
|
||||
if err := waitUntilHealthy(name, resolver, healthPath); err != nil {
|
||||
log.Printf("[Scale] error waiting for function %s to become ready, error: %s\n", name, err)
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// waitUntilHealthy blocks until the healthPath returns a HTTP 200 for the
|
||||
// IP address resolved for the given function.
|
||||
// Maximum retries: 100
|
||||
// Delay between each attempt: 20ms
|
||||
// A custom path can be set via an annotation in the function's spec:
|
||||
// com.openfaas.health.http.path: /handlers/ready
|
||||
//
|
||||
func waitUntilHealthy(name string, resolver proxy.BaseURLResolver, healthPath string) error {
|
||||
endpoint, err := resolver.Resolve(name)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
host, port, _ := net.SplitHostPort(endpoint.Host)
|
||||
u, err := url.Parse(fmt.Sprintf("http://%s:%s%s", host, port, healthPath))
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
// Try to hit the health endpoint and block until
|
||||
// ready.
|
||||
attempts := 100
|
||||
pause := time.Millisecond * 20
|
||||
for i := 0; i < attempts; i++ {
|
||||
req, err := http.NewRequest(http.MethodGet, u.String(), nil)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
res, err := http.DefaultClient.Do(req)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
if res.Body != nil {
|
||||
res.Body.Close()
|
||||
}
|
||||
|
||||
if res.StatusCode != http.StatusOK {
|
||||
return fmt.Errorf("unexpected health status: %d", res.StatusCode)
|
||||
}
|
||||
|
||||
if err == nil {
|
||||
break
|
||||
}
|
||||
|
||||
time.Sleep(pause)
|
||||
}
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
@ -10,14 +10,14 @@ import (
|
||||
"path"
|
||||
"strings"
|
||||
|
||||
"github.com/containerd/containerd"
|
||||
"github.com/openfaas/faas-provider/types"
|
||||
provider "github.com/openfaas/faasd/pkg/provider"
|
||||
)
|
||||
|
||||
const secretFilePermission = 0644
|
||||
const secretDirPermission = 0755
|
||||
|
||||
func MakeSecretHandler(store provider.Labeller, mountPath string) func(w http.ResponseWriter, r *http.Request) {
|
||||
func MakeSecretHandler(c *containerd.Client, mountPath string) func(w http.ResponseWriter, r *http.Request) {
|
||||
|
||||
err := os.MkdirAll(mountPath, secretFilePermission)
|
||||
if err != nil {
|
||||
@ -31,13 +31,13 @@ func MakeSecretHandler(store provider.Labeller, mountPath string) func(w http.Re
|
||||
|
||||
switch r.Method {
|
||||
case http.MethodGet:
|
||||
listSecrets(store, w, r, mountPath)
|
||||
listSecrets(c, w, r, mountPath)
|
||||
case http.MethodPost:
|
||||
createSecret(w, r, mountPath)
|
||||
createSecret(c, w, r, mountPath)
|
||||
case http.MethodPut:
|
||||
createSecret(w, r, mountPath)
|
||||
createSecret(c, w, r, mountPath)
|
||||
case http.MethodDelete:
|
||||
deleteSecret(w, r, mountPath)
|
||||
deleteSecret(c, w, r, mountPath)
|
||||
default:
|
||||
w.WriteHeader(http.StatusBadRequest)
|
||||
return
|
||||
@ -46,11 +46,11 @@ func MakeSecretHandler(store provider.Labeller, mountPath string) func(w http.Re
|
||||
}
|
||||
}
|
||||
|
||||
func listSecrets(store provider.Labeller, w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
func listSecrets(c *containerd.Client, w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
|
||||
lookupNamespace := getRequestNamespace(readNamespaceFromQuery(r))
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(store, lookupNamespace)
|
||||
valid, err := validNamespace(c, lookupNamespace)
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
@ -63,15 +63,8 @@ func listSecrets(store provider.Labeller, w http.ResponseWriter, r *http.Request
|
||||
|
||||
mountPath = getNamespaceSecretMountPath(mountPath, lookupNamespace)
|
||||
|
||||
files, err := os.ReadDir(mountPath)
|
||||
if os.IsNotExist(err) {
|
||||
bytesOut, _ := json.Marshal([]types.Secret{})
|
||||
w.Write(bytesOut)
|
||||
return
|
||||
}
|
||||
|
||||
files, err := ioutil.ReadDir(mountPath)
|
||||
if err != nil {
|
||||
fmt.Printf("Error Occured: %s \n", err)
|
||||
http.Error(w, err.Error(), http.StatusInternalServerError)
|
||||
return
|
||||
}
|
||||
@ -85,7 +78,7 @@ func listSecrets(store provider.Labeller, w http.ResponseWriter, r *http.Request
|
||||
w.Write(bytesOut)
|
||||
}
|
||||
|
||||
func createSecret(w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
func createSecret(c *containerd.Client, w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
secret, err := parseSecret(r)
|
||||
if err != nil {
|
||||
log.Printf("[secret] error %s", err.Error())
|
||||
@ -125,7 +118,7 @@ func createSecret(w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
}
|
||||
}
|
||||
|
||||
func deleteSecret(w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
func deleteSecret(c *containerd.Client, w http.ResponseWriter, r *http.Request, mountPath string) {
|
||||
secret, err := parseSecret(r)
|
||||
if err != nil {
|
||||
log.Printf("[secret] error %s", err.Error())
|
||||
|
||||
@ -1,9 +1,6 @@
|
||||
package handlers
|
||||
|
||||
import (
|
||||
"encoding/json"
|
||||
"fmt"
|
||||
"io/ioutil"
|
||||
"net/http"
|
||||
"net/http/httptest"
|
||||
"os"
|
||||
@ -13,8 +10,6 @@ import (
|
||||
"testing"
|
||||
|
||||
"github.com/openfaas/faas-provider/types"
|
||||
"github.com/openfaas/faasd/pkg"
|
||||
provider "github.com/openfaas/faasd/pkg/provider"
|
||||
)
|
||||
|
||||
func Test_parseSecret(t *testing.T) {
|
||||
@ -166,87 +161,3 @@ func TestSecretCreation(t *testing.T) {
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestListSecrets(t *testing.T) {
|
||||
mountPath, err := os.MkdirTemp("", "test_secret_creation")
|
||||
if err != nil {
|
||||
t.Fatalf("unexpected error while creating temp directory: %s", err)
|
||||
}
|
||||
|
||||
defer os.RemoveAll(mountPath)
|
||||
|
||||
cases := []struct {
|
||||
name string
|
||||
verb string
|
||||
namespace string
|
||||
labels map[string]string
|
||||
status int
|
||||
secretPath string
|
||||
secret string
|
||||
err string
|
||||
expected []types.Secret
|
||||
}{
|
||||
{
|
||||
name: "Get empty secret list for default namespace having no secret",
|
||||
verb: http.MethodGet,
|
||||
status: http.StatusOK,
|
||||
secretPath: "/test-fn/foo",
|
||||
secret: "bar",
|
||||
expected: make([]types.Secret, 0),
|
||||
},
|
||||
{
|
||||
name: "Get empty secret list for non-default namespace having no secret",
|
||||
verb: http.MethodGet,
|
||||
status: http.StatusOK,
|
||||
secretPath: "/test-fn/foo",
|
||||
secret: "bar",
|
||||
expected: make([]types.Secret, 0),
|
||||
namespace: "other-ns",
|
||||
labels: map[string]string{
|
||||
pkg.NamespaceLabel: "true",
|
||||
},
|
||||
},
|
||||
}
|
||||
|
||||
for _, tc := range cases {
|
||||
t.Run(tc.name, func(t *testing.T) {
|
||||
labelStore := provider.NewFakeLabeller(tc.labels)
|
||||
|
||||
handler := MakeSecretHandler(labelStore, mountPath)
|
||||
|
||||
path := "http://example.com/foo"
|
||||
if len(tc.namespace) > 0 {
|
||||
path = path + fmt.Sprintf("?namespace=%s", tc.namespace)
|
||||
}
|
||||
req := httptest.NewRequest(tc.verb, path, nil)
|
||||
w := httptest.NewRecorder()
|
||||
|
||||
handler(w, req)
|
||||
|
||||
resp := w.Result()
|
||||
if resp.StatusCode != tc.status {
|
||||
t.Fatalf("want status: %d, but got: %d", tc.status, resp.StatusCode)
|
||||
}
|
||||
|
||||
if resp.StatusCode != http.StatusOK && w.Body.String() != tc.err {
|
||||
t.Fatalf("want error message: %q, but got %q", tc.err, w.Body.String())
|
||||
}
|
||||
|
||||
body, err := ioutil.ReadAll(resp.Body)
|
||||
if err != nil {
|
||||
t.Fatalf("can't read response of list %v", err)
|
||||
}
|
||||
|
||||
var res []types.Secret
|
||||
err = json.Unmarshal(body, &res)
|
||||
|
||||
if err != nil {
|
||||
t.Fatalf("unable to unmarshal %q, error: %v", string(body), err)
|
||||
}
|
||||
|
||||
if !reflect.DeepEqual(res, tc.expected) {
|
||||
t.Fatalf("want response: %v, but got: %v", tc.expected, res)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
@ -43,7 +43,7 @@ func MakeUpdateHandler(client *containerd.Client, cni gocni.CNI, secretMountPath
|
||||
namespace := getRequestNamespace(req.Namespace)
|
||||
|
||||
// Check if namespace exists, and it has the openfaas label
|
||||
valid, err := validNamespace(client.NamespaceService(), namespace)
|
||||
valid, err := validNamespace(client, namespace)
|
||||
if err != nil {
|
||||
http.Error(w, err.Error(), http.StatusBadRequest)
|
||||
return
|
||||
|
||||
@ -5,9 +5,10 @@ import (
|
||||
"net/http"
|
||||
"path"
|
||||
|
||||
"github.com/containerd/containerd"
|
||||
|
||||
"github.com/openfaas/faasd/pkg"
|
||||
faasd "github.com/openfaas/faasd/pkg"
|
||||
provider "github.com/openfaas/faasd/pkg/provider"
|
||||
)
|
||||
|
||||
func getRequestNamespace(namespace string) string {
|
||||
@ -29,11 +30,12 @@ func getNamespaceSecretMountPath(userSecretPath string, namespace string) string
|
||||
|
||||
// validNamespace indicates whether the namespace is eligable to be
|
||||
// used for OpenFaaS functions.
|
||||
func validNamespace(store provider.Labeller, namespace string) (bool, error) {
|
||||
func validNamespace(client *containerd.Client, namespace string) (bool, error) {
|
||||
if namespace == faasd.DefaultFunctionNamespace {
|
||||
return true, nil
|
||||
}
|
||||
|
||||
store := client.NamespaceService()
|
||||
labels, err := store.Labels(context.Background(), namespace)
|
||||
if err != nil {
|
||||
return false, err
|
||||
|
||||
@ -1,25 +0,0 @@
|
||||
package provider
|
||||
|
||||
import "context"
|
||||
|
||||
// Labeller can return labels for a namespace from containerd.
|
||||
type Labeller interface {
|
||||
Labels(ctx context.Context, namespace string) (map[string]string, error)
|
||||
}
|
||||
|
||||
//
|
||||
// FakeLabeller can be used to fake labels applied on namespace to mark
|
||||
// them valid/invalid for openfaas functions
|
||||
type FakeLabeller struct {
|
||||
labels map[string]string
|
||||
}
|
||||
|
||||
func NewFakeLabeller(labels map[string]string) Labeller {
|
||||
return &FakeLabeller{
|
||||
labels: labels,
|
||||
}
|
||||
}
|
||||
|
||||
func (s *FakeLabeller) Labels(ctx context.Context, namespace string) (map[string]string, error) {
|
||||
return s.labels, nil
|
||||
}
|
||||
@ -8,8 +8,6 @@ import (
|
||||
"os"
|
||||
"path"
|
||||
"sort"
|
||||
"strconv"
|
||||
"strings"
|
||||
|
||||
"github.com/alexellis/k3sup/pkg/env"
|
||||
"github.com/compose-spec/compose-go/loader"
|
||||
@ -28,8 +26,7 @@ import (
|
||||
)
|
||||
|
||||
const (
|
||||
// workingDirectoryPermission user read/write/execute, group and others: read-only
|
||||
workingDirectoryPermission = 0744
|
||||
workingDirectoryPermission = 0644
|
||||
)
|
||||
|
||||
type Service struct {
|
||||
@ -148,28 +145,6 @@ func (s *Supervisor) Start(svcs []Service) error {
|
||||
Type: "bind",
|
||||
Options: []string{"rbind", "rw"},
|
||||
})
|
||||
|
||||
// Only create directories, not files.
|
||||
// Some files don't have a suffix, such as secrets.
|
||||
if len(path.Ext(mnt.Src)) == 0 &&
|
||||
!strings.HasPrefix(mnt.Src, "/var/lib/faasd/secrets/") {
|
||||
// src is already prefixed with wd from an earlier step
|
||||
src := mnt.Src
|
||||
fmt.Printf("Creating local directory: %s\n", src)
|
||||
if err := os.MkdirAll(src, workingDirectoryPermission); err != nil {
|
||||
if !errors.Is(os.ErrExist, err) {
|
||||
fmt.Printf("Unable to create: %s, %s\n", src, err)
|
||||
}
|
||||
}
|
||||
if len(svc.User) > 0 {
|
||||
uid, err := strconv.Atoi(svc.User)
|
||||
if err == nil {
|
||||
if err := os.Chown(src, uid, -1); err != nil {
|
||||
fmt.Printf("Unable to chown: %s to %d, error: %s\n", src, uid, err)
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
Reference in New Issue
Block a user